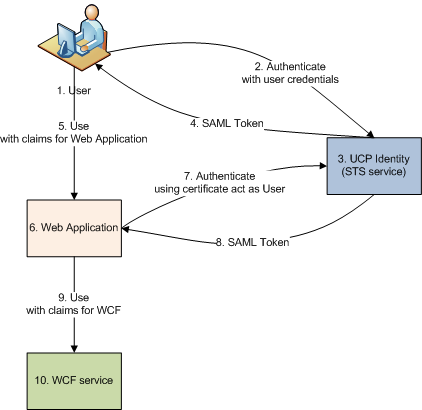
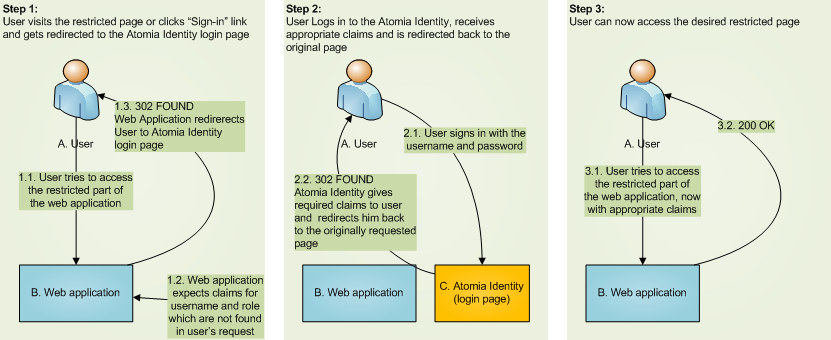
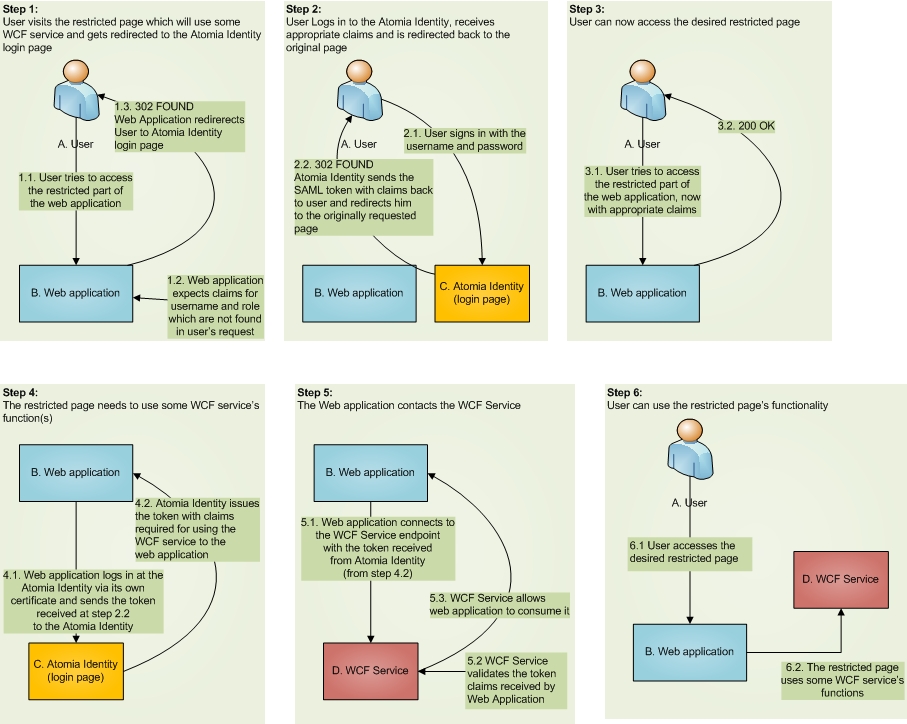
We are starting from conficuration like this:
As we can see we are starting with one WCF service
ICoreService
that does not need any authentication.
To enable authentication using
Atomia Identity
in this file we will add config section for
microsoft.identity
In this config file few things are important to note:
line 09 - We define with which issuer our WCF application has trusted relation.
line 17 - Defines value of which token type will be interpreted as username
line 18 - Defines value of which token type will be interpreted as users role
Now, we should configure our service to use federated authentication
On the STS side we should add RP (Rely party) certificate and inform STS that for given URI should use that certificate.
This is done in two steps:
1. Set which RpCertProvider to use for given RP URI
2. For AtomiaRpCertProvider set how to find certificate
Of course, you will have to install that certificate on given location.
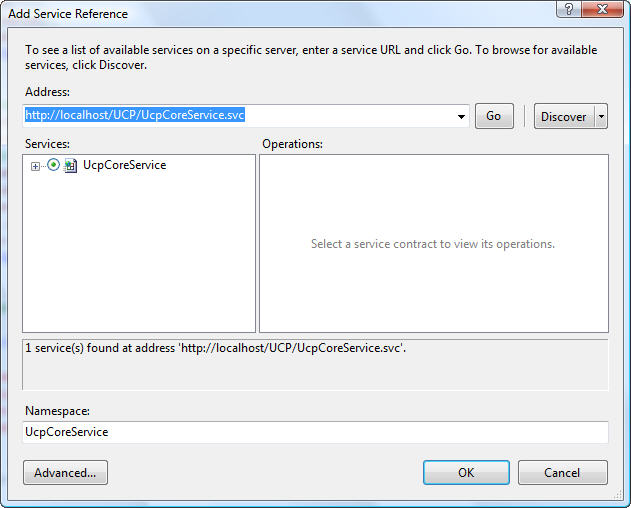
If we now update service reference on client side Visual Studio will generate config file like:
If you look line 24 you will see that is set what is address of STS server but its not set how to authenticate to this service. We will need to update that line like:
Now we should add new bindingConfiguration:
With this binding configuration we have set how the client will be authenticated to the STS.

![[Important]](important.png)